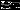Facebook Messenger for MacOS contained valid hardcoded FB access token (employee's token?)
At summer I decided to test Facebook Messenger for MacOS. Grepped all urls from code and started to analyze them. Quickly I noticed few urls on image with "access_token" value:
Cool! Interesting is this token still valid?
I opened https://developers.facebook.com/tools/debug/accesstoken/?access_token= and got confirmation: the token is valid!
I stopped experiments and rapidly sent report to Facebook Team.
So, be careful and attentive when you investigate hardcoded data inside apps ;)
- Facebook Messenger v. 97.11.116 (97.11.116.283083801) for MacOS
- Submitted: 27.07.2021 10:08AM
- Triaged: 27.07.2021 12:36AM
- Fixed: 27.07.2021 12:45AM (token became invalid, may be system automatically invalidated the token or Facebook team did it)
- Fix notification: 04.08.2021
- Reward: $500 (+$125 bonus) 08.09.2021